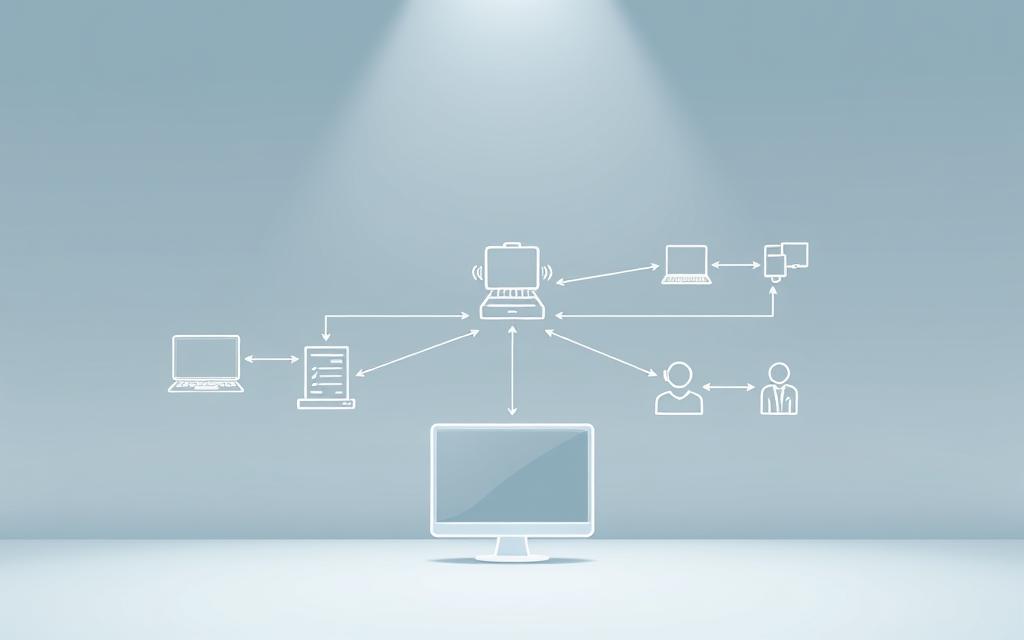
A computer-based information system (CBIS) is key to today’s businesses. It evolved from old ledger systems to now turn data into useful insights. Laudon’s work shows it helps make better decisions at all levels.
It has five main parts. Hardware gives the system power, and software handles tasks. Data is kept accurate, and rules help keep things consistent. People are also vital for understanding results and coming up with new ideas.
Big retailers use these systems a lot. They check stock levels, track money, and make shopping personal. This move from paper to digital shows how important they are today.
Getting it right means combining tech skills with human insight. Together, they form adaptive frameworks that tackle big problems. This includes managing supply chains and meeting customer needs.
Understanding Computer-Based Information Systems
Today, companies use digital systems to turn data into useful information. This part looks at how computer-based information systems (CBIS) have changed how we make decisions. They’ve moved from using paper to using smart data systems.
Defining the Digital Backbone
A CBIS is made up of hardware, software, and people working together. It’s different from keeping records by hand because it can process data in real-time. It helps make decisions and improve how things work.
From Filing Cabinets to Cloud Storage
The story of CBIS started in the 1960s with systems for handling transactions. Banks were among the first to switch from paper to digital records. Here are some important moments:
- 1970s: Management information systems (MIS) were introduced
- 1990s: Enterprise resource planning (ERP) software became common
- 2010s: Cloud-based analytics tools were developed
Cross-Industry Implementation
Now, CBIS are used in many fields. The NHS uses systems to keep up-to-date medical records, cutting down on mistakes. Stores use them to manage stock and predict what to order next.
These systems fit into Laudon’s framework for decision-making:
| Operational Level | Tactical Level | Strategic Level |
|---|---|---|
| Transaction processing | Resource allocation | Market expansion analysis |
| Daily sales tracking | Staff scheduling | Five-year forecasting |
Essential Hardware Components
Today’s businesses need connected hardware to run their key operations. These systems are the heart of data-driven work, needing careful setup to ensure they work well, stay safe, and can grow.
Central Processing Units and Servers
Modern CPUs are like digital workhorses, handling up to 5.7 billion tasks per second in top models. They do more than just calculate, they also decide which tasks to do first.
- They handle many tasks at once
- They adjust power use to save energy
- They have built-in security to spot threats fast
Role in Data Processing
Big banks like JPMorgan Chase use adaptive CPU clusters to handle 450 million transactions daily. These setups can shift tasks during busy times, keeping responses quick.
Enterprise Server Configurations
Top data centres now offer 99.995% uptime, thanks to Tier IV setups. Leading enterprise server setups mix:
| Component | Financial Sector | Healthcare Systems |
|---|---|---|
| Redundancy | N+2 architecture | Geo-distributed nodes |
| Cooling | Liquid immersion systems | Adiabatic solutions |
| Security | FIPS 140-2 modules | HIPAA-compliant encryption |
Input/Output Device Ecosystems
The NHS uses palm-vein scanners to check patient identities 2.3 million times a day. This tech cut down on mistakes by 89% in tests.
Biometric Scanners in Modern Systems
Now, banks use different biometrics together:
- They check faces and make sure they’re real
- They look at how you type
- They check your voice
Multi-Functional Office Devices
Canon’s imagePROGRAF TX series shows how devices can do many things at once. They print, scan, and even shred documents safely in one go.
Storage Infrastructure Solutions
Hybrid cloud solutions are key for storing data now. They mix AWS Snowball Edge with NetApp arrays on site. This meets GDPR rules and keeps data accessible.
Cloud Storage vs Physical Servers
| Criteria | AWS Cloud | On-Premise |
|---|---|---|
| Deployment Speed | 15-minute provisioning | 6-8 week lead time |
| Compliance | Shared responsibility model | Full internal control |
| Cost Profile | Operational expenditure | Capital expenditure |
Disaster Recovery Systems
Goldman Sachs has a Active-Active-Active system for data. It ensures no data is lost, working across three zones. Their system uses:
- Blockchain for real-time checks
- Secure S3 storage
- Safe magnetic tape backups
Software Architecture Fundamentals
Today, companies use layered software architectures to link hardware with business goals. This structure helps grow and keep things safe, which is key in finance and energy. It’s built on three main parts: system software, special apps, and middleware.
System Software Essentials
System software is at the heart of digital systems, with operating systems managing hardware. For example, JP Morgan Chase uses Linux kernel optimisations for fast trade execution. They focus on quick data processing during market times.
Security Protocol Management
Now, fighting cyber threats involves both machines and humans. The 2023 OAS framework suggests:
- Adding biometric checks for access
- Encrypting data in real-time
- Regularly updating security patches
Application Software Types
Today, enterprise software is more than just tools. It’s becoming a key asset. Companies are picking between custom-made platforms and modular systems, each with its own benefits.
Custom CRM Solutions
Salesforce’s Lightning Platform shows how CRM customisation boosts sales. Target, for example, sped up lead conversion by:
- Using AI for recommendations
- Creating special pricing for dealers
- Building mobile tools for field services
ERP System Implementations
Even though SAP S/4HANA is big in manufacturing, ERP implementation challenges are real. A Deloitte study found 43% of projects go over budget because of:
- Old system problems
- Staff not wanting to change
- Complicated data moves
Middleware Integration Strategies
National Grid’s SCADA update shows how vital middleware is. They linked old systems to Azure IoT Hub with:
- Protocol translators
- APIs for connections
- Edge computing for safety
This mix cut outage response times by 68% while keeping old systems.
Data Management Frameworks
Today’s businesses need structured ways to turn raw data into useful insights. They use frameworks to manage and protect their data. These frameworks also help meet legal standards.
Database Management Systems
Modern systems mix precise relational databases with NoSQL scalability. For example, NHS trusts use Oracle for patient records. This ensures data accuracy. At the same time, MongoDB handles imaging data with flexibility.
SQL vs NoSQL Architectures
SQL databases are strict for financial data. NoSQL is better for fast changes in e-commerce. Amazon shows how document stores update data models without stopping.
Tesco uses a mix of Hadoop and Snowflake for data storage and analysis. This combination helps with both historical analysis and daily operations.
Information Processing Models
Businesses pick processing methods based on how quickly they need decisions:
| Model | Use Case | Latency |
|---|---|---|
| Real-time analytics | Tesco’s inventory tracking | <1 second |
| Batch processing | HMRC tax calculations | 24-48 hours |
Real-Time Analytics Systems
Platforms like Apache Kafka power dashboards for traders and emergency teams. They focus on speed over detail.
Batch Processing Workflows
Government agencies use scheduled tasks for big jobs. The UK’s tax authority handles millions of returns overnight with old COBOL systems and new ETL pipelines.
Data Security Protocols
Now, following rules is as important as running smoothly. The Financial Conduct Authority requires AES-256 encryption for fintech platforms.
GDPR Compliance Measures
UK companies must do several things:
- Set up portals for data access requests
- Automate data retention
- Check third-party data processors
Encryption Standards
Banks use strong encryption like Kyber-1024 and AES-256 encryption. This protects customer data from new threats.
Human and Organisational Elements
While advanced technology is key, it’s human expertise and organisational adaptability that really matter. Success comes from improving workforce skills, governance, and managing change well. These areas are often overlooked in favour of tech talk.
User Competency Requirements
The digital skills gap is a big problem for companies. The NHS Digital’s upskilling program has trained over 15,000 staff in data analytics. GCHQ’s CyberFirst also helps by:
- Offering specialist apprenticeships for 16-18 year olds
- Supporting university programs
- Hosting national cybersecurity competitions
IT Governance Structures
Good decision-making is essential for tech to meet business goals. The COBIT framework is used by 68% of FTSE 100 companies. It works well with ITIL 4 service management. Important governance parts include:
| Framework | Primary Application | Key Feature |
|---|---|---|
| COBIT 2019 | Enterprise-wide governance | Risk management integration |
| ITIL 4 | Service delivery | Value chain optimisation |
| GDPR Alignment | Data protection | Post-Brexit compliance |
Change Management Processes
National Rail’s ERP migration is a great example of good change management. They got 94% of users on board with a phased approach. Success factors were:
- Stakeholder workshops during planning
- Real-time performance dashboards
- Mobile training for depot staff
After Brexit, the need for flexible governance models has grown. This is true for data protection and handling information across borders.
Strategic Priorities for Modern Information Ecosystems
Computer-based information systems are key to making businesses run smoothly and decisions based on data. As we look to the future, we see quantum computing and advanced encryption becoming more important. Companies like IBM and Microsoft are already working on new ways to keep data safe.
Businesses need to think about how new technologies fit with what they already have. Can old systems handle AI and analytics without risking security? Are current IT rules ready for automated workflows? These questions show why it’s vital to plan upgrades carefully.
For companies wanting to stay ahead, working with IASME-certified cybersecurity experts is a good move. They offer advice on updating systems. Regular checks on storage and how different parts work together help keep up with changing rules. This way, businesses can use new tools like predictive analytics and machine learning.